Advanced Cyber Attack Vectors
Explore Advanced Cyber Attack Vectors learn how hackers exploit systems, escalate privileges, and stay hidden, plus key defenses for cybersecurity learners.
Table of Contents
- Advanced Cyber Attack Vectors
- Climbing the Ladder Privilege Escalation
- Staying Inside Persistence Mechanisms
- The Clean Getaway Evading Detection
- From Defense to Design Why Structure Matters
- Key Takeaways
- Conclusion
Introduction The Hidden Science of Intrusion
Every day, organizations face digital intruders who exploit not just code but also human habits. From phishing emails to kernel-level rootkits, each stage of an attack reveals how technology can be turned against itself.
This week’s lesson explains how cybercriminals break in, move through networks, and remain invisible, providing you with both offensive and defensive insights.
If you’re new to security concepts, start with our overview: History of Cybersecurity. It shows how threats evolved from simple viruses to state-level attacks.

Gaining the Foothold How Hackers Enter Systems
After reconnaissance and scanning, the attacker launches the first real strike exploiting weaknesses to deliver a payload that grants access. This is where the cyber war truly begins.
1.1 Core Attack Vectors Explained
| Attack Vector | What It Means | Example in Action | Defense Strategy |
|---|---|---|---|
| Vulnerability Exploitation | Using flaws like buffer overflows or unpatched apps to execute code. | Apache Struts exploit used in Equifax breach. | Continuous patch management & automated scanning. |
| Password and Credential Attacks | Guessing or reusing stolen credentials. | Brute-force on RDP servers. | Enforce MFA + password rotation. |
| Social Engineering | Manipulating people to reveal access. | Fake invoice phishing emails. | Conduct security awareness training. |
| Misconfiguration | Exploiting open ports or default accounts. | Public MongoDB without auth. | Regular configuration audits & PoLP. |
Attackers rarely rely on one vector they chain several together for reliability.
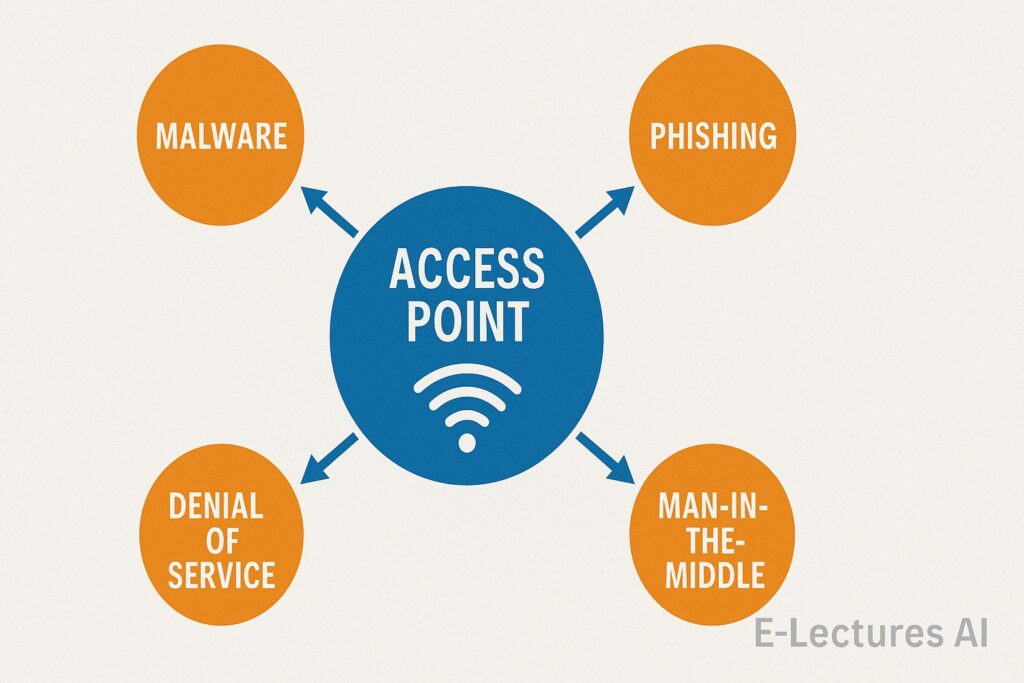
Technology can block code, not human curiosity that’s why social engineering remains the hardest to stop.
📎 Internal Link: See how structured logic improves security decisions → Introduction to Data Structures 2025
Climbing the Ladder Privilege Escalation
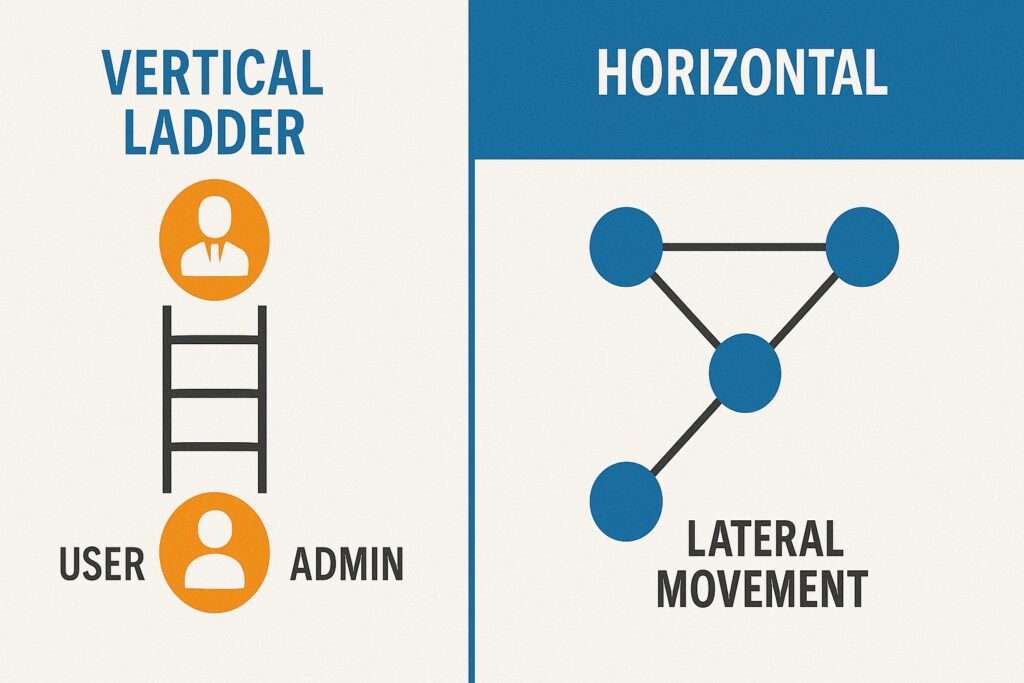
Initial access usually gives low-level rights. To control an entire network, attackers must escalate privileges either vertically (gain admin/root) or horizontally (move between users).
2.1 Vertical vs Horizontal Escalation
- Vertical (“Upward Power”): User → Administrator/Root → Total Control.
- Horizontal (“Sideways Expansion”): Same privilege level → different machines or accounts.
2.2 Common Techniques
| Technique | Focus Area | Attack Summary | Defense Tip |
|---|---|---|---|
| Kernel Exploits | OS core | Inject code exploiting OS bug. | Keep OS fully patched. |
| Abusing SUID/SGID | Linux/Unix tools | Run shells as root via privileged binaries. | Remove SUID bits from non-essential files. |
| Vulnerable Services | Apps with elevated rights | Use service’s power to run malware. | Configure least privilege services. |
| Credential Dumping (Mimikatz) | Windows memory | Extract password hashes or tokens. | Enable LSA Protection & Credential Guard. |
Staying Inside Persistence Mechanisms
A true hacker doesn’t just break in they build a home inside the system. Persistence ensures re-entry even after reboots or patching.
Backdoors and Remote Access Trojans (RATs)
These create secret login paths or encrypted tunnels back to the attacker, often disguised as legitimate services.
Rootkits The Art of Invisibility
Rootkits alter system processes so malware and logs vanish from view. Kernel-level rootkits load before security tools, making them virtually undetectable.
Startup Abuse
Attackers exploit:
- Windows Registry Run Keys to auto-launch payloads at boot.
- Scheduled Tasks / Cron Jobs to reactivate malware periodically.

Persistence = Stealth + Automation. The longer an intruder stays, the more valuable data they steal.
The Clean Getaway Evading Detection
Before leaving, attackers erase all footprints. This cover-up phase determines how long an attack stays undiscovered.
| Evasion Technique | What Hackers Do | Countermeasure |
|---|---|---|
| Log Tampering / Deletion | Remove evidence of access. | Use Write-Once Read-Many (SIEM) logging. |
| Timestamp Modification | Match malicious files to legit timestamps. | Enable File Integrity Monitoring (FIM). |
| Traffic Hiding (Covert Channels) | Send data via DNS/ICMP tunnels. | Apply Deep Packet Inspection (DPI). |

Modern defenses focus on behavioral anomalies and AI-based detection that identify patterns humans might miss.
From Defense to Design Why Structure Matters
In both computing and security, structure is strength.
A system built on logical, well-defined rules is easier to secure much like data structures define how information is stored and retrieved efficiently.
📎 Read next: Digital Logic Design — Foundation of Computing
Learn how logic gates and boolean algebra mirror decision-making in security policies.
Key Takeaways
- Initial Access often relies on human error.
- Privilege Escalation turns a small mistake into a network breach.
- Persistence Mechanisms ensure hackers survive system updates.
- Evading Detection requires deep knowledge of logs and forensics.
- Continuous Defense is built on structured learning and logical design.
Conclusion
Hackers thrive on blind spots both technical and psychological.
By understanding each phase of an attack, students and professionals can learn to think like an attacker and build systems that defend like a fortress.
Combining knowledge from Cybersecurity, Data Structures, and Digital Logic Design creates a complete mindset for the AI-powered future of security.
“Security is not a product; it’s a process of constant learning and adaptation.”