Information Security
Introduction to Information Security: Learn the foundational concepts, the importance of safeguarding data in the digital world, and key terms like threats, vulnerabilities, and controls. Essential for understanding InfoSec basics.
What is Information Security?
Information Security (InfoSec) refers to the practices and technologies designed to protect sensitive data and systems from unauthorized access, disclosure, alteration, destruction, or disruption. In the digital world, where data is a critical asset for organizations and individuals alike, InfoSec plays a vital role in ensuring that information remains safe and secure.
InfoSec encompasses a wide range of practices, including risk management, encryption, authentication, and compliance with legal frameworks. The primary goal of InfoSec is to safeguard Confidentiality, Integrity, and Availability (CIA Triad), which are essential pillars of security.

Lecture 1 – Introduction to Programming Paradigms
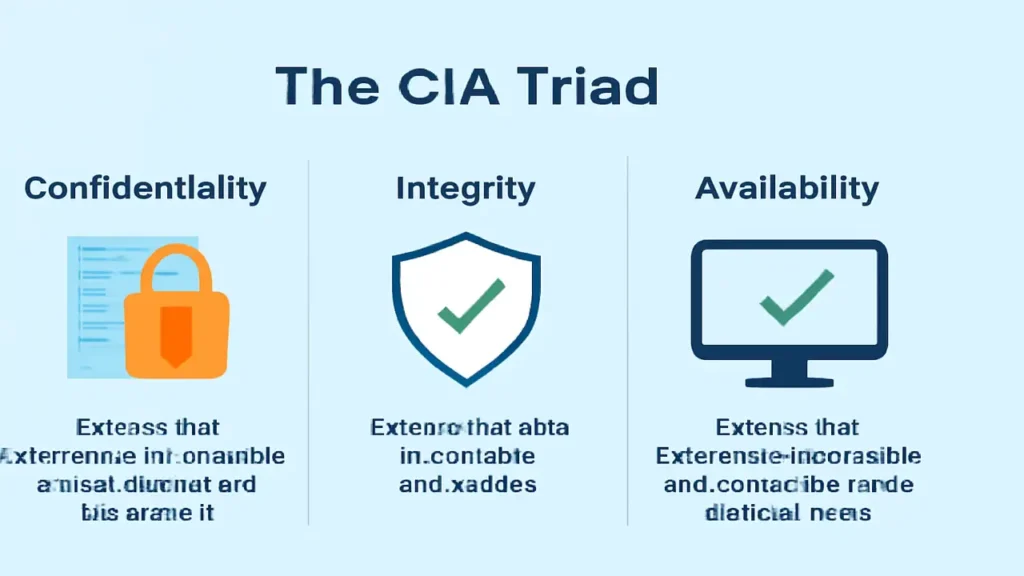
The CIA Triad (Confidentiality, Integrity, and Availability)
The CIA Triad is the cornerstone of Information Security. It consists of three principles:
- Confidentiality: Ensures that information is accessible only to those authorized to access it. For example, personal health data should only be accessible to medical professionals and not to unauthorized individuals.
- Integrity: Ensures that data is accurate, reliable, and protected from unauthorized modification. It ensures that the information remains unchanged during transmission or storage unless altered by authorized entities.
- Availability: Ensures that information is available and accessible to authorized users whenever needed. For example, a website must remain operational so that users can access necessary data anytime.
Importance in the Digital World
In today’s digital age, information is created, processed, and stored in vast quantities. From financial transactions to social media interactions and government data, almost everything we do relies on digital systems and the data they manage. This digital shift has made information security more critical than ever before.
As the volume of data increases, so do the risks. Cyberattacks are becoming more sophisticated, with hackers targeting personal information, business operations, and government systems. Without proper security measures in place, sensitive information can be exposed, stolen, or manipulated.
- Cyberattacks like ransomware, phishing, and data breaches are prevalent threats that organizations face daily.
- Data Privacy: Protecting individuals’ personal data is now a legal requirement in many parts of the world (e.g., GDPR in Europe, CCPA in California).
- Financial Loss: A single data breach can lead to millions of dollars in financial losses due to theft, recovery costs, and fines.
- Reputation Damage: If a company fails to protect customer data, it risks losing the trust of its clients and partners, resulting in long-term reputational harm.
As we rely more on digital systems for work, communication, and entertainment, information security becomes a critical aspect of maintaining privacy, trust, and operational stability.

Key Terms and Concepts
To understand Information Security, it’s essential to know some basic terms and concepts:
- Threat: Any potential danger to information or systems. Threats can be natural (e.g., earthquakes) or man-made (e.g., hacking).
- Vulnerability: A weakness in a system that can be exploited by a threat. For example, outdated software can have security flaws that hackers can exploit.
- Risk: The potential loss or damage that can occur when a threat exploits a vulnerability. It’s calculated based on the likelihood of the threat occurring and the severity of its impact.
- Control: Measures taken to reduce risks, such as firewalls, encryption, and access controls. Controls can be preventive, detective, or corrective.
- Malware: Malicious software designed to damage or disrupt a system. This includes viruses, worms, and ransomware.
- Phishing: A social engineering attack where cybercriminals impersonate trusted entities to steal sensitive information like login credentials or financial details.
- Authentication: The process of verifying the identity of a user, device, or system to ensure only authorized entities have access.
- Access Control: Policies and technologies used to regulate who can access information and resources. It ensures that only authorized individuals can access specific data.

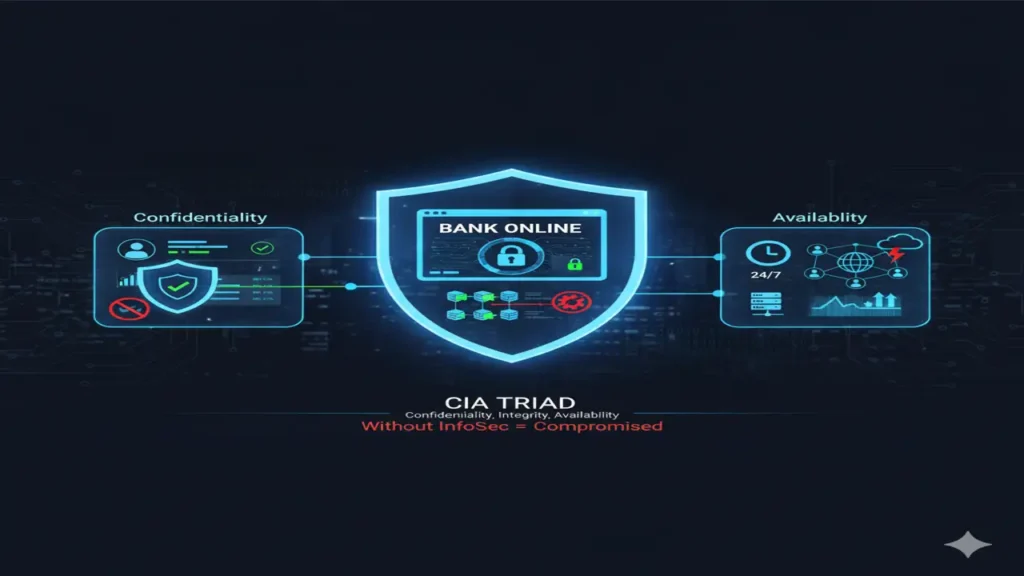
Real-World Example
Imagine you are managing a bank’s online banking system.
- Confidentiality: You ensure that customers’ account details, such as balances and transaction history, are only accessible to them and not to unauthorized users.
- Integrity: You implement measures to make sure that once a transaction is made, it cannot be altered or tampered with by a hacker or malicious software.
- Availability: You ensure that the bank’s online services are up and running 24/7, providing customers with access to their accounts whenever they need it.
Without proper InfoSec measures, all these essential services could be compromised by attackers.
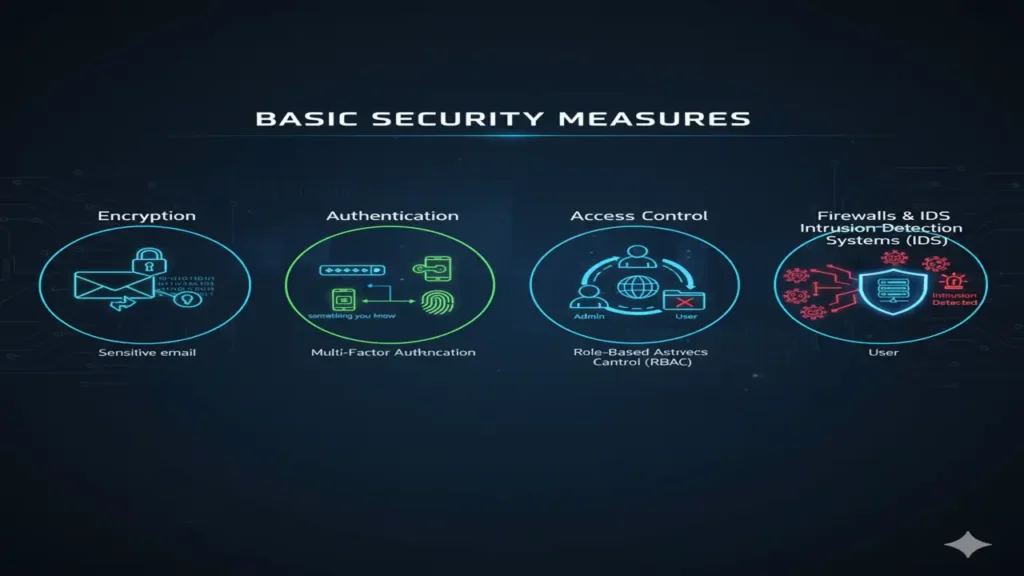
Basic Security Measures
Here are some common security practices that ensure the protection of data:
- Encryption: The process of converting data into a code to prevent unauthorized access. For example, when sending a sensitive email, encryption ensures that only the recipient can read the message.
- Authentication: Verifying the identity of users or devices. Multi-factor authentication (MFA) is a common method that combines something the user knows (password), something the user has (smartphone), and something the user is (fingerprint).
- Access Control: Managing who has access to data and systems. Role-based access control (RBAC) ensures that only authorized users can access certain resources based on their roles within the organization.
- Firewalls and Intrusion Detection Systems (IDS): Protecting networks and systems from unauthorized access and detecting potential security breaches.
Summary of Lecture 1
| Concept | Meaning | Example |
|---|---|---|
| Information Security | Protecting sensitive data and systems | Using encryption and authentication |
| Confidentiality | Ensuring data is only accessible by authorized users | Secure login for online banking |
| Integrity | Ensuring data is accurate and untampered | Preventing changes to transaction records |
| Availability | Ensuring data is available when needed | Keeping systems operational 24/7 |
| Threat, Vulnerability, Risk | Terms related to security issues | Malware threats exploiting outdated software |
| Control | Measures to reduce risks | Firewalls, encryption, authentication |
“Information security is not just about protecting data it’s about empowering the future. As students, you’re the next generation of defenders, innovators, and leaders in a world that’s increasingly digital. Your knowledge and skills will help secure the foundations of trust, privacy, and progress in every system we build. Keep learning, stay curious, and remember: with great knowledge comes great responsibility!”