Learn secure software design and development principles, secure coding practices, common vulnerabilities, and security testing methods in the SDLC.
Introduction
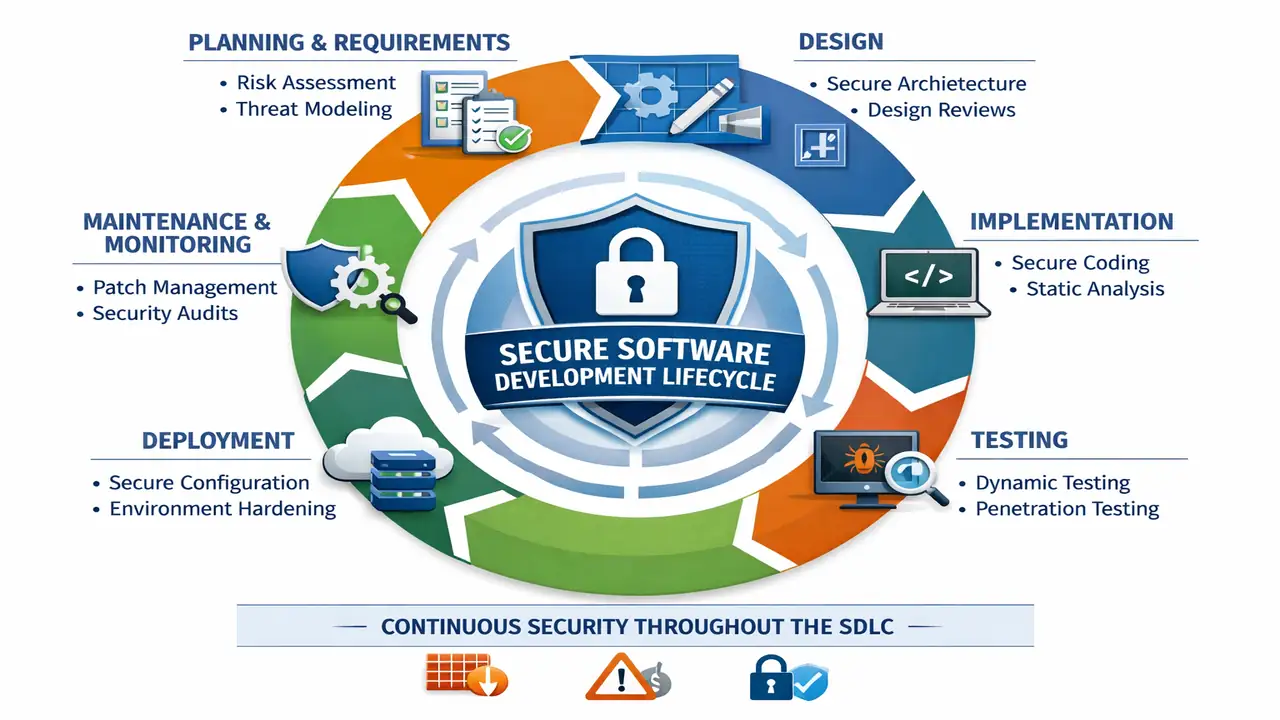
In today’s digital environment, software systems are constantly exposed to cyber threats ranging from data breaches to full-scale infrastructure compromise. Secure Software Design and Development focuses on integrating security controls into every stage of the Software Development Life Cycle (SDLC) rather than treating security as a final testing activity.
Modern applications rely on distributed architectures, cloud services, APIs, and third-party libraries. This complexity increases the attack surface, making secure design and disciplined coding practices essential. This article provides a detailed explanation of secure software design principles, secure coding practices, common vulnerabilities, and industry-standard security testing methodologies.
Secure Software Design: Why Design-Level Security Matters
Security flaws introduced at the design stage are often the most expensive and difficult to fix later. A weak architecture can make even well-written code insecure.
Principle of Least Privilege
Least Privilege ensures that users, services, and processes operate with only the permissions strictly required to perform their tasks.
Why it matters
- Limits damage in case of compromise
- Prevents privilege escalation attacks
- Reduces lateral movement inside systems
Example
A database service that only performs read operations should not have permission to modify tables or manage users.
Defense in Depth
Defense in Depth means implementing multiple layers of security controls instead of relying on a single mechanism.
Typical layers include
- Network security (firewalls, segmentation)
- Application security (authentication, authorization)
- Data security (encryption at rest and in transit)
- Monitoring and logging
If one layer fails, the remaining layers continue to protect the system.
Fail-Safe Defaults
Fail-safe defaults ensure that access is denied unless explicitly allowed.
Key idea
- Default state = no access
- Permissions must be intentionally granted
Practical benefit
If a system component crashes or misconfigures, it does not accidentally expose sensitive data or functionality.
Economy of Mechanism
This principle emphasizes simplicity in design.
Why simplicity improves security
- Easier to understand and audit
- Fewer hidden interactions
- Lower chance of configuration errors
Complex security mechanisms often introduce more vulnerabilities than they solve.
Open Design
Open Design assumes attackers understand how the system works.
Important clarification
- Security must rely on strong controls, not secrecy
- Algorithms, architectures, and protocols should remain secure even if publicly known
This principle aligns with modern cryptographic and open-source security practices.
Secure Coding Practices: Turning Design into Safe Code
Even a strong design can fail if implementation is careless. Secure coding reduces the risk of exploitable weaknesses.
Input Validation and Sanitization
All input from users, APIs, files, or external systems must be treated as untrusted.
Best practices
- Use allow-lists instead of block-lists
- Validate data type, length, format, and range
- Reject unexpected input early
This directly prevents injection attacks such as SQL injection and command injection.
Output Encoding
Output encoding ensures that data is treated as content, not executable code.
Common risks prevented
- Cross-Site Scripting (XSS)
- HTML injection
- JavaScript injection
Encoding must match the output context (HTML, JavaScript, URL, JSON).
Authentication and Session Security
Authentication verifies identity, while session management maintains that identity securely.
Secure practices
- Use Multi-Factor Authentication
- Store passwords using slow hashing algorithms
- Use random, high-entropy session tokens
- Expire sessions properly and invalidate on logout
Weak session management is one of the most exploited attack vectors.
Secure Error Handling and Logging
Errors must be handled carefully to avoid leaking internal system details.
Correct approach
- Show generic messages to users
- Log detailed errors securely on the server
- Protect logs from unauthorized access
Information disclosure through error messages often assists attackers in crafting exploits.
Software Vulnerabilities and Risk Awareness
Despite best practices, vulnerabilities still occur. Awareness and structured mitigation are essential.
Common Categories of Vulnerabilities
- Broken access control
- Cryptographic failures
- Injection attacks
- Security misconfiguration
- Insecure dependencies
- Authentication and authorization flaws
These risks are widely recognized as critical threats in modern applications.
Security Testing Throughout the SDLC
Security testing should be continuous and layered, just like security controls.
Static Application Security Testing (SAST)
- Analyzes source code without execution
- Identifies logic errors and insecure coding patterns
- Best used during development
Strength
Early detection at low cost
Dynamic Application Security Testing (DAST)
- Tests running applications
- Simulates real attacker behavior
- Identifies runtime issues
Strength
Realistic external attack perspective
Software Composition Analysis (SCA)
- Scans third-party libraries and dependencies
- Identifies known vulnerabilities and license risks
Strength
Protects against supply-chain attacks
Interactive Application Security Testing (IAST)
- Combines static and dynamic analysis
- Observes application behavior during execution
Strength
High accuracy with contextual insights
Penetration Testing and Manual Review
- Conducted by security professionals
- Focuses on complex attack chains and business logic flaws
Strength
Highest realism and depth of analysis
Conclusion
Secure Software Design and Development is not a single task or tool but a continuous, disciplined process. Security must begin at the design stage, be reinforced through secure coding practices, and validated using multiple testing methodologies. Organizations that integrate security into every phase of development build software that is resilient, trustworthy, and sustainable in the face of evolving threats.