Learn blockchain architecture, cryptographic foundations, cybersecurity attacks, and real-world use cases in secure decentralized systems.
Introduction
Blockchain Architecture plays a critical role in modern cybersecurity by providing decentralized, tamper-resistant, and transparent systems for data storage and transaction management. Originally developed for digital currencies, blockchain technology is now widely applied in cybersecurity domains such as identity management, IoT security, data integrity assurance, and distributed system protection.
This article explains the fundamental architecture of blockchain, its cryptographic foundations, common cybersecurity attacks targeting blockchain networks, and real-world cybersecurity use cases.
Key Concepts in Blockchain Architecture
Blockchain
Blockchain is a decentralized and distributed ledger technology where transactions are recorded across multiple nodes in a peer-to-peer network. Once data is written to the blockchain, altering it becomes practically impossible without modifying all subsequent blocks and achieving network consensus.
Cybersecurity significance
- Eliminates centralized control
- Prevents unauthorized data modification
- Enhances trust in untrusted environments
Immutability
Immutability refers to the property that data cannot be changed or deleted once it is added to the blockchain. This is enforced using cryptographic hash functions that link each block to its predecessor.
Security benefit
Any attempt to alter data changes the hash, instantly exposing tampering.
Decentralization
Decentralization distributes control and data across multiple nodes, removing reliance on a central authority.
Why it matters for security
- Eliminates Single Point of Failure (SPOF)
- Improves resilience against cyberattacks
- Increases fault tolerance
Secure Software Design and Development: A Comprehensive Guide for Modern Applications
Consensus Mechanism
A consensus mechanism is a fault-tolerant protocol that enables network participants to agree on the state of the blockchain.
Common examples
- Proof of Work (PoW)
- Proof of Stake (PoS)
Cybersecurity role
Consensus prevents fraudulent transactions and ensures data consistency across the network.
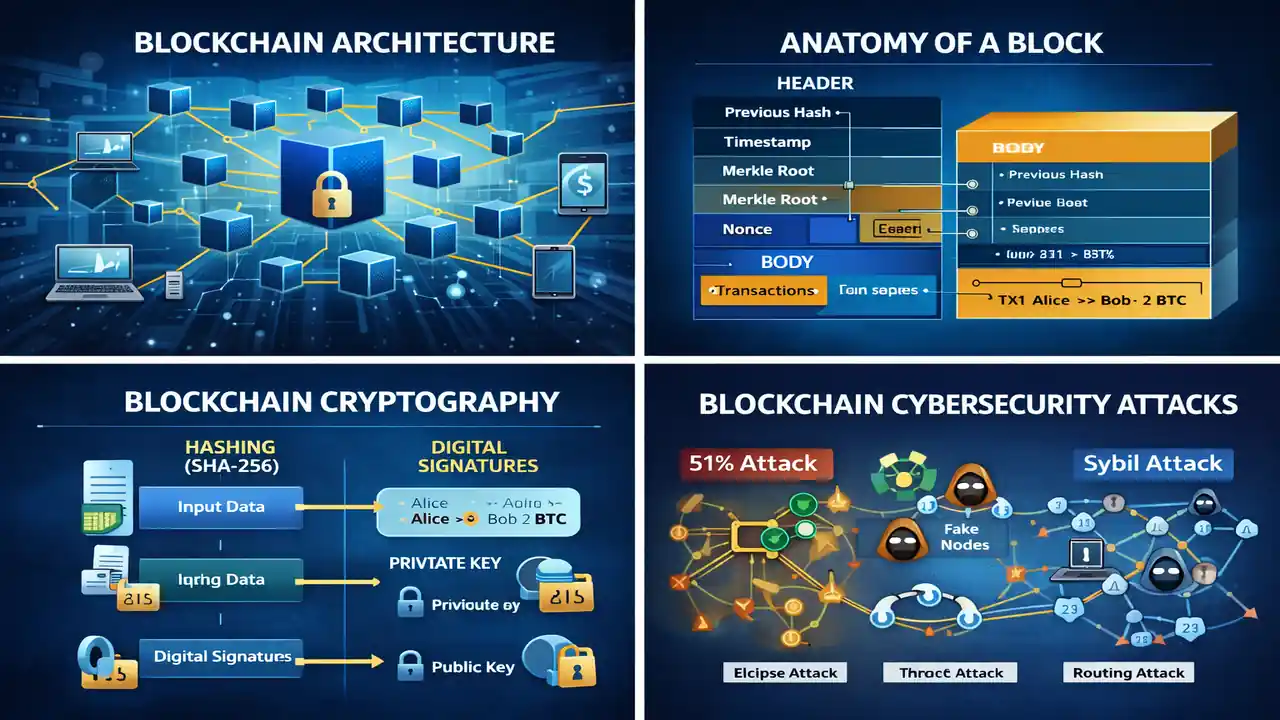
Anatomy of a Blockchain Block
Each block consists of two major parts: the Block Header and the Block Body.
Key Components and Their Security Roles
Previous Hash
Stores the cryptographic hash of the previous block.
- Links blocks together
- Any modification breaks the chain integrity
Timestamp
Records when the block was created.
- Maintains chronological order
- Prevents replay attacks
Merkle Root
A single hash representing all transactions within the block.
- Enables fast verification
- Ensures transaction integrity
Nonce
A random number used during mining (especially in PoW).
- Introduces computational difficulty
- Protects against brute-force attacks
Transactions
The actual data or asset transfers stored in the block body.
- Represents the secured payload
- Protected through cryptographic verification
Cryptographic Foundations of Blockchain Security
Hashing (SHA-256)
Hashing converts input data into a fixed-length output using a one-way function.
Security properties
- Deterministic
- Collision resistant
- Irreversible
Hashing ensures data integrity and immutability.
Digital Signatures
Blockchain uses asymmetric cryptography with public and private keys.
How it works
- Transactions are signed using a private key
- Verified using the corresponding public key
Security benefits
- Authentication
- Non-repudiation
- Transaction integrity
Merkle Tree
A Merkle Tree is a hierarchical structure of hashes.
Advantages
- Efficient data verification
- Reduced storage requirements
- Enables lightweight blockchain clients
Cybersecurity Attacks on Blockchain Networks
Although blockchain is inherently secure, it is not immune to attacks.
51% Attack
Occurs when a single entity controls more than half of the network’s mining or validation power.
Impact
- Transaction reversal
- Double spending
- Network manipulation
Sybil Attack
An attacker creates multiple fake identities to influence the network.
Risk
- Manipulates consensus
- Undermines trust
Eclipse Attack
A target node is isolated from the network by controlling its connections.
Consequences
- Node receives false blockchain data
- Facilitates double-spending attacks
Routing Attack
Attackers intercept or manipulate data during transmission.
Effect
- Network partitioning
- Temporary denial of consensus
Blockchain Applications in Cybersecurity
Identity Management
Blockchain enables Self-Sovereign Identity (SSI), allowing users to control their own digital identities without central authorities.
IoT Security
Decentralized communication reduces reliance on centralized servers, limiting the scale of IoT botnet attacks.
Data Integrity Assurance
Blockchain ensures logs, system records, and machine learning datasets remain untampered.
DDoS Mitigation
Decentralized hosting and DNS systems eliminate single attack targets, increasing resilience against DDoS attacks.
Conclusion
Blockchain architecture introduces powerful cybersecurity advantages through decentralization, cryptographic integrity, and fault-tolerant consensus mechanisms. While it mitigates many traditional security risks, understanding blockchain-specific attacks is essential. When implemented correctly, blockchain provides a robust foundation for secure digital systems across multiple industries.