18 Types of AI Agents & LLM Models (2025 Guide)
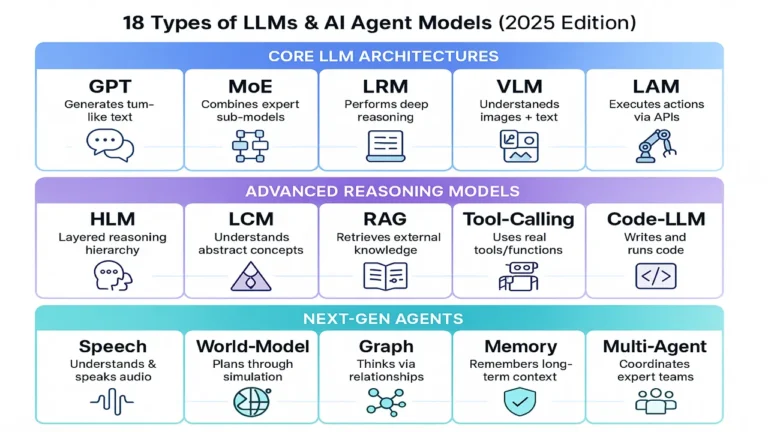
Clear, up-to-date guide to 18 types of AI agents and LLM architectures what they are, when to use them, stacks, pitfalls, and FAQs. What is an AI Agent? An AI agent is a system that (1) understands inputs, (2) reasons…