Understanding Malware
Learn about the three core types of malware Trojans, Viruses, and Worms. Discover how they spread, how analysts detect them, and how to defend your system using static and dynamic malware analysis.
What Is Malware and Why It Matters
Malware, short for malicious software, refers to any program intentionally designed to harm a computer, server, or network. Cyber attackers use malware to steal data, disrupt systems, or gain unauthorized access. Understanding malware is crucial because it forms the engine behind most modern cyber attacks from data breaches to ransomware outbreaks.

How Hackers Break In and Stay Hidden: Inside Advanced Cyber Attack Vectors
The Core Three: Trojans, Viruses, and Worms
Malware comes in many forms, but three types dominate cybersecurity discussions: Trojans, Viruses, and Worms. Each has unique behaviors and purposes.
| Type | How It Spreads | Needs a Host File | Main Purpose |
|---|---|---|---|
| Trojan Horse | Relies on deception. Disguised as legitimate software (like “free games” or “updates”). | ❌ No | Steals data or creates backdoors. |
| Virus | Attaches to legitimate files and spreads when they are opened. | ✅ Yes | Corrupts data or damages systems. |
| Worm | Self-replicates across networks automatically. | ❌ No | Consumes bandwidth or drops payloads. |
Worms are the most dangerous because they spread without human interaction, moving across networks at lightning speed.

The Powerful Anatomy of Cyber Threats & Attack Vectors (Part 1)
How Malware Spreads: Propagation Techniques
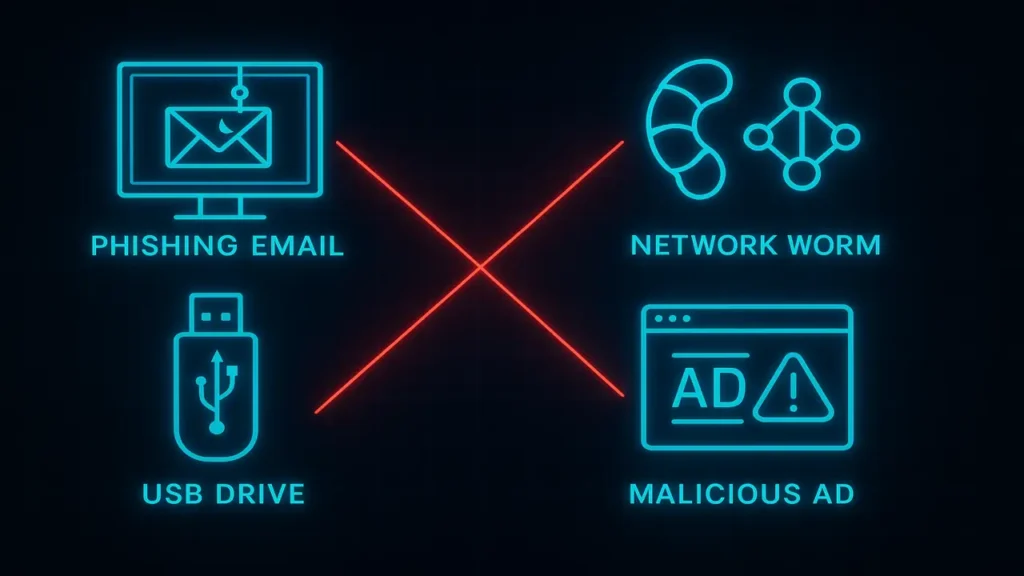
Malware infiltrates systems using multiple infection vectors methods that exploit human error, outdated software, or poor configurations.
Email Attachments (Malspam)
Fake emails contain infected attachments disguised as invoices or resumes.
Defense: Use email filters and train users to detect phishing.
Drive-by Downloads
Malware installs automatically when visiting infected websites.
Defense: Keep browsers updated and use endpoint protection tools.
Network Exploits
Worms spread via vulnerabilities in network services like SMB or RDP.
Defense: Patch management and network segmentation are key.
Removable Media
Infected USB drives spread malware when connected to another system.
Defense: Disable autorun and limit external device use.
Malvertising
Malicious code hidden inside legitimate-looking online ads.
Defense: Implement strong Content Security Policies (CSP).
Malware Analysis: How Experts Study the Enemy
Cybersecurity analysts use two main methods to investigate suspicious files Static and Dynamic analysis.
Static Malware Analysis
This method examines malware without running it. Analysts inspect the file’s code, metadata, and structure to identify Indicators of Compromise (IoCs) such as file paths, IP addresses, and API calls.
Tools: PEView, Dependency Walker, MD5/SHA256 checksum utilities.
Limitation: Obfuscated malware may hide its real behavior.

Dynamic Malware Analysis
Here, the malware is executed inside a sandbox an isolated, virtual environment to observe real behavior like registry changes or network communication.
Tools: Cuckoo Sandbox, Wireshark, ProcMon.
Limitation: Some malware detects it’s inside a VM and hides its malicious actions.

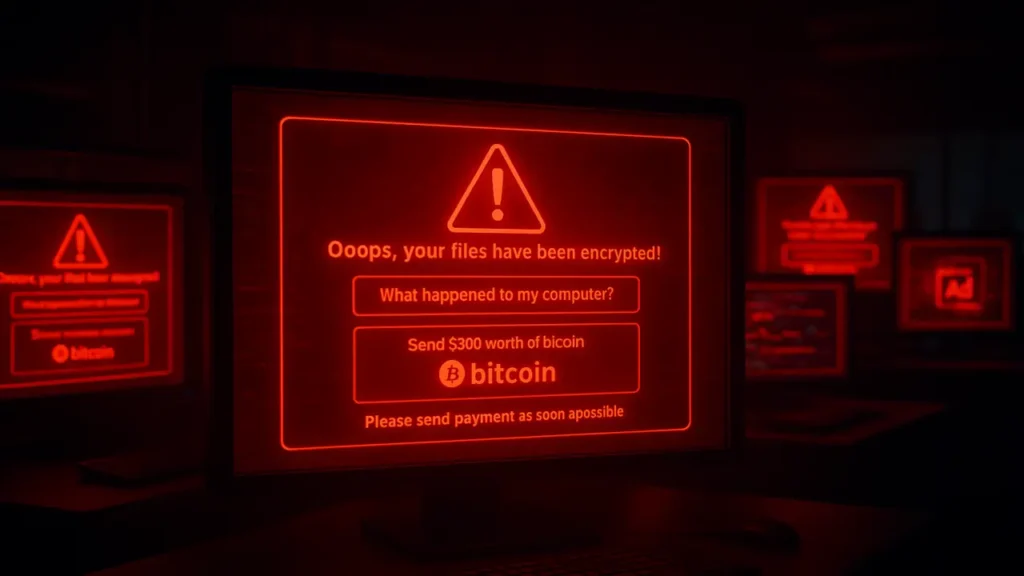
Real-World Example: WannaCry Ransomware Worm (2017)
In 2017, WannaCry crippled over 200,000 computers worldwide within hours. It combined worm-like propagation with ransomware encryption, exploiting a Windows SMB vulnerability called EternalBlue. Once infected, users’ files were encrypted, and a Bitcoin ransom demand appeared.
Lesson:
Even one unpatched system can trigger a global cyber outbreak.
Final Thoughts
Malware continues to evolve from simple trojans to advanced, AI-driven cyber weapons. To stay secure, keep your systems updated, use trusted antivirus tools, and practice safe browsing habits. Remember: cybersecurity begins with awareness.