Cyber Threats & Attack Vectors
Learn the fundamentals of cyber threats & attack vectors from hacking concepts and ethical hacking principles to reconnaissance, scanning, and enumeration techniques used in cybersecurity today.
Table of Contents
- Cyber Threats & Attack Vectors
- Introduction – Understanding the Core Concepts
- Hacking: Concepts, Types, and Phases
- Ethical Hacking Principles
- Footprinting and Reconnaissance
- Network Scanning and Enumeration
- Conclusion
Introduction – Understanding the Core Concepts
Before we dive into complex cyberattacks, it’s important to understand the key elements that make up the foundation of cyber threats and attack vectors.
- Threat: A potential danger that exploits weaknesses and causes harm (e.g., a hacker attempting to break into a network).
- Vulnerability: A flaw in design, code, or policy that can be exploited (e.g., weak password or unpatched software).
- Attack Vector: The method used by a hacker to gain unauthorized access (e.g., phishing email or open port).

For a broader understanding of how cybersecurity has evolved over time, you can explore the article The History of Cybersecurity – From Creeper to Cybercrime Laws in Pakistan
Hacking: Concepts, Types, and Phases
Hacking Concept
In cybersecurity, hacking refers to gaining unauthorized access to a system or data. It can be used for both malicious and defensive purposes depending on the hacker’s intent.
Types of Hackers (The Hats)
- White Hat (Ethical Hackers): Work legally to test and strengthen systems.
- Black Hat (Criminal Hackers): Operate illegally for personal gain or destruction.
- Gray Hat: Find vulnerabilities without permission but may disclose them for good.

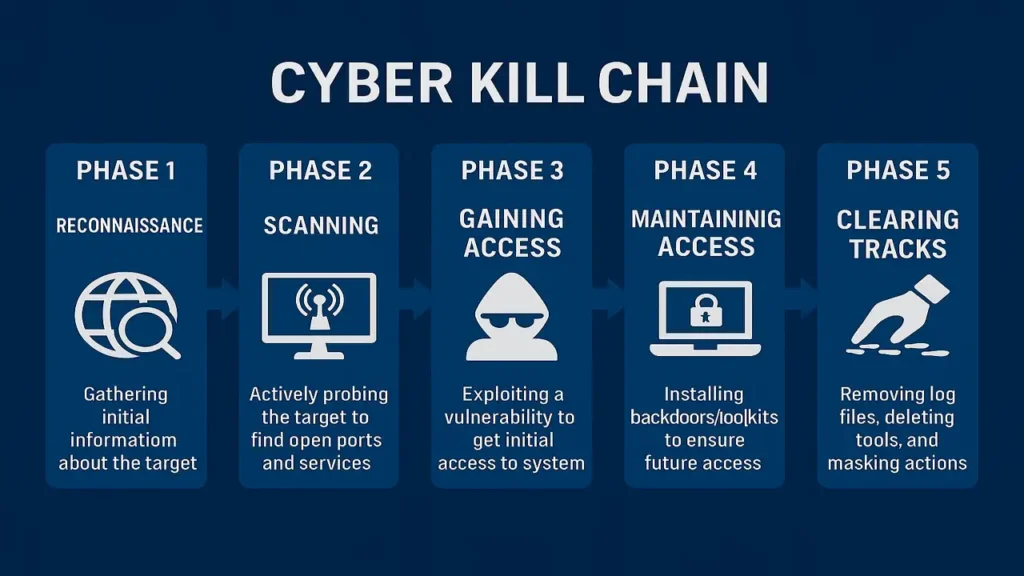
The Five Phases of Hacking (Kill Chain)
Every attack follows a sequence known as the “kill chain”:
- Reconnaissance – Gathering target info.
- Scanning – Probing for open ports/services.
- Gaining Access – Exploiting vulnerabilities.
- Maintaining Access – Installing backdoors for persistence.
- Clearing Tracks – Deleting logs to avoid detection.
To strengthen your computing fundamentals, read our detailed lecture on the Number System in Digital Logic Design
Ethical Hacking Principles
Ethical hacking simulates attacks legally to evaluate system security. These are the key principles that define it:
- Legal Authorization: Permission must be written and approved before testing.
- Scope Definition: Specifies what systems are in or out of bounds.
- No Damage: The goal is to identify weaknesses, not to disrupt services.
- Reporting & Confidentiality: All findings remain private and documented.
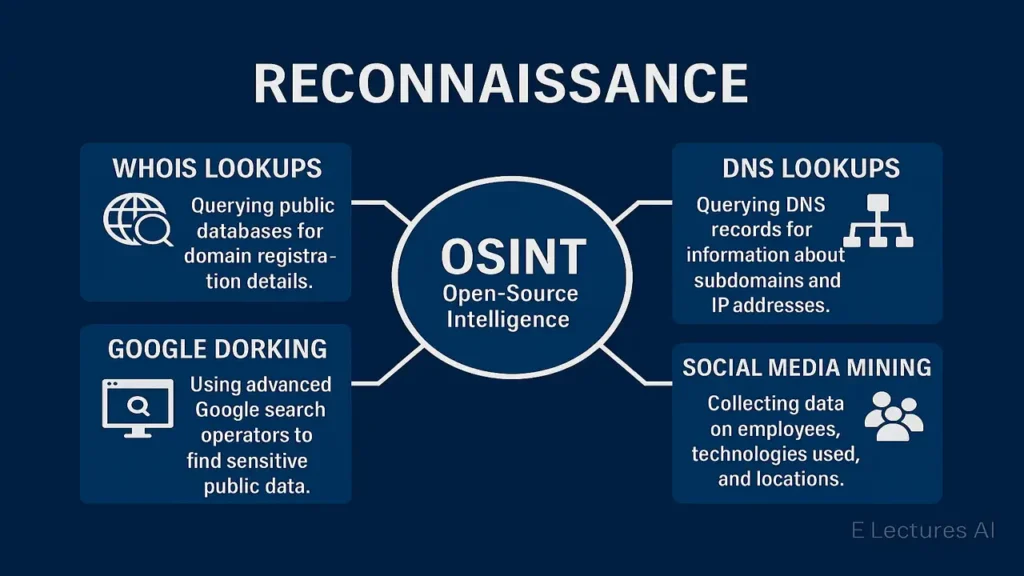
Footprinting and Reconnaissance
The first phase in most cyber threats and attack vectors is footprinting a passive process of gathering information about the target.
Common Techniques:
- WHOIS Lookups: To find domain registration details.
- DNS Lookups: Discover subdomains and IPs.
- Google Dorking: Search for exposed configurations.
- Social Media Mining: Collect employee or tech stack details.
- Archived Sites: Using tools like Wayback Machine to find old vulnerabilities.
To build a solid programming foundation, check out the Introduction to Data Structures
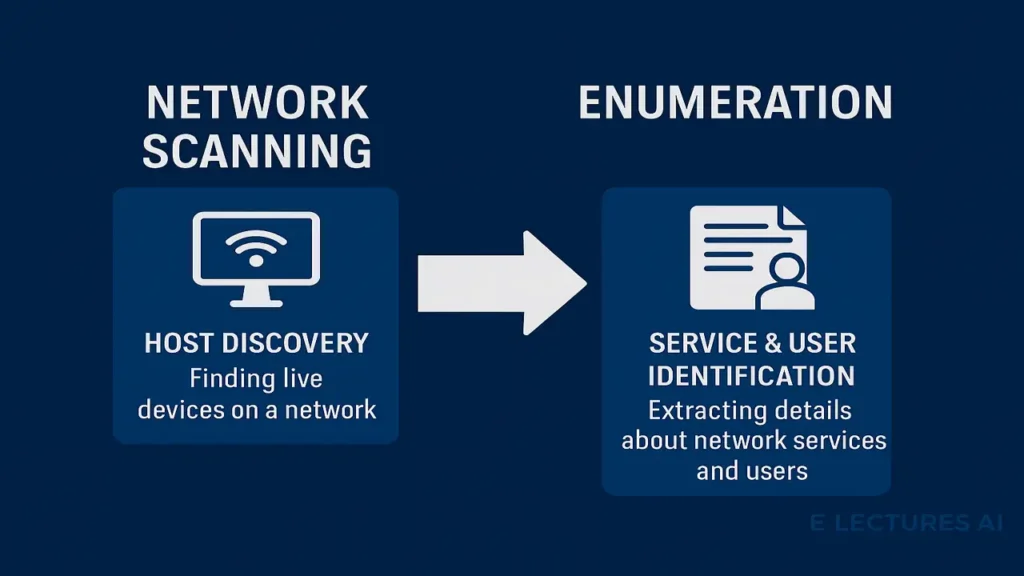
Network Scanning and Enumeration
After reconnaissance, hackers move into active scanning probing networks to uncover live hosts and running services.
Network Scanning Includes:
- Host Discovery (Ping Sweeps): Identify active IP addresses.
- Port Scanning: Detect open or filtered ports using tools like Nmap.
Enumeration Focuses On:
- Service Version Detection: Identify exact software versions (e.g., Apache 2.4.41).
- OS Fingerprinting: Determine operating systems via network probes.
- User/Group Enumeration: Extract usernames or group data via SNMP and other protocols.
Conclusion
The study of cyber threats and attack vectors reveals how attackers think and how defenders can anticipate their moves. By mastering these core concepts, future cybersecurity professionals can protect systems more effectively.