Symmetric and asymmetric cryptography, AES-GCM, RSA/ECC, key exchange, and hybrid encryption with practical tips, pitfalls, and commands.
Definitions
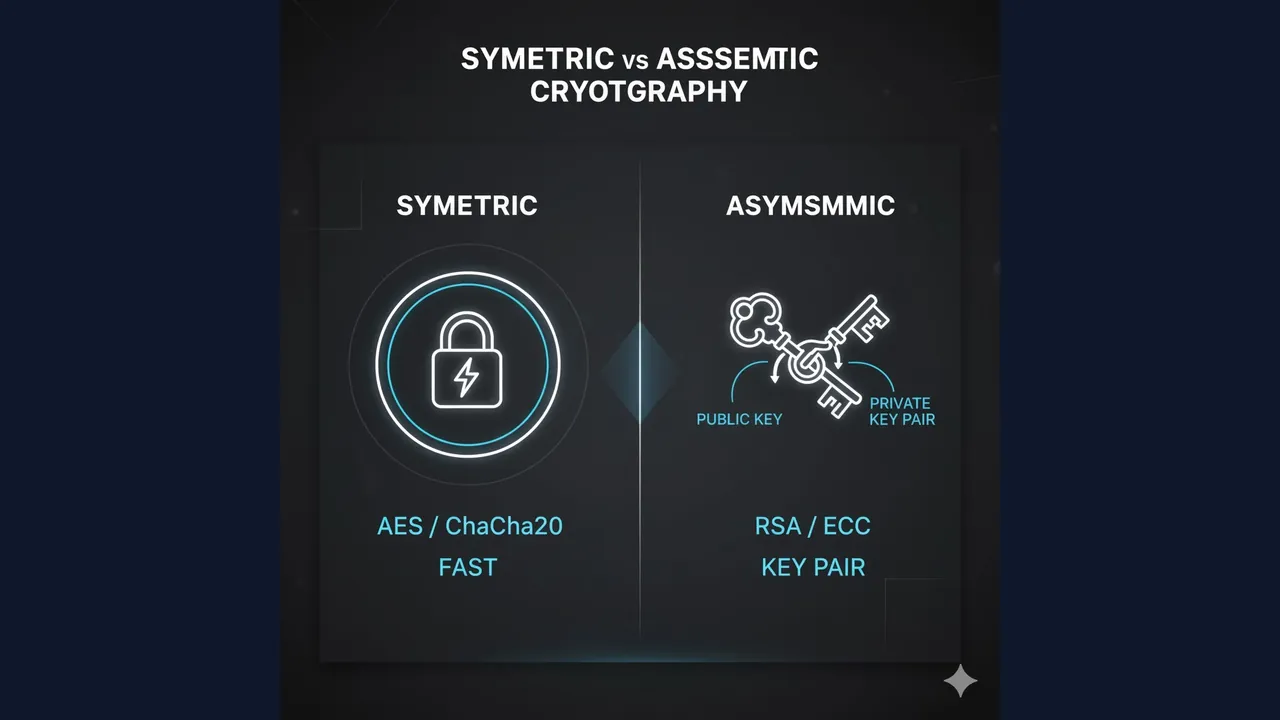
- Symmetric cryptography: Same secret key to encrypt and decrypt (fast, lightweight).
- Asymmetric cryptography: Public key encrypts/verifies; private key decrypts/signs (easier distribution, slower).
Symmetric Cryptography
Common Algorithms
- AES (block cipher; 128-bit block; keys 128/192/256)
- ChaCha20 (stream cipher; great on mobile/low-power CPUs)
Modes of Operation (for AES)
- GCM (AEAD: encryption + integrity). Preferred.
- CBC (needs padding + separate MAC; avoid new designs).
- CTR (stream-like; must pair with MAC).
Nonces/IVs
- Unique per message. Never reuse a nonce with the same key (catastrophic with GCM/CTR).
Performance
- Very fast, constant-time implementations available. Ideal for bulk data encryption.
Typical Uses
- Disk/database encryption, API payloads after session setup, backups, secure messaging content.
Asymmetric Cryptography
Core Families
- RSA (based on factoring). Common key sizes: 2048/3072 bits.
- ECC (elliptic curves): X25519 for key exchange, Ed25519 for signatures, P-256 widely supported.
Capabilities
- Encryption / Key Encapsulation (KEM): send a secret to someone’s public key.
- Digital Signatures: prove authenticity with private key; anyone verifies with public key.
- Key Exchange: two parties derive a shared secret (e.g., X25519 ECDH) without sharing private keys.
Performance
- Slower than symmetric; used for small objects (session keys, signatures), not bulk data.
Typical Uses
- TLS handshakes, software signing, SSH keys, email signing/encryption (PGP), certificate infrastructure.
Symmetric vs Asymmetric Comparison
| Property | Symmetric | Asymmetric |
|---|---|---|
| Keys | One shared secret | Public key + private key |
| Speed | Very fast | Slower (CPU-heavy) |
| Typical Data Size | Bulk data | Small items (session keys, signatures) |
| Key Distribution | Hard (share secretly) | Easy (publish public key) |
| Examples | AES-GCM, ChaCha20-Poly1305 | RSA-2048/3072, X25519, Ed25519 |
| Integrity | AEAD modes include MAC | Signatures provide authenticity |
| Common Use | After session established | Establish session / verify identity |
Lecture 2 – Security Design Principles 15 Rules for Building Secure Systems
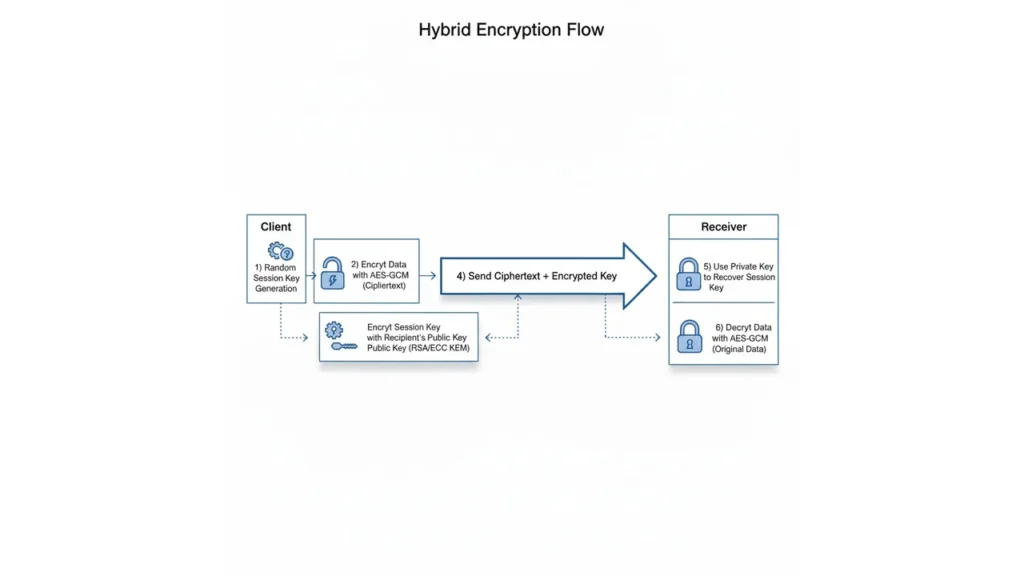
Hybrid Encryption
Most real systems use both:
- Use asymmetric crypto to agree on a fresh symmetric key (e.g., X25519 key exchange or RSA key encapsulation).
- Use that symmetric key with AES-GCM or ChaCha20-Poly1305 to encrypt all subsequent data.
This gives you easy key distribution + high performance (how TLS works).
Key Management Essentials
- Generation: use trusted libraries; high-quality randomness.
- Derivation: use KDFs (HKDF, PBKDF2/Argon2 for passwords).
- Rotation: change keys on a schedule or after incidents.
- Storage: keep symmetric keys in KMS/HSM; never hard-code.
- Separation: different keys for encryption vs signing.
- Lifetimes: short-lived session keys; revoke on suspicion.
Mini Lab (OpenSSL quick start)
Encrypt a file with AES-256-GCM (password-based):
# Encrypt
openssl enc -aes-256-gcm -pbkdf2 -salt -in report.pdf -out report.enc
# Decrypt
openssl enc -d -aes-256-gcm -pbkdf2 -in report.enc -out report.pdfGenerate Ed25519 signing key and sign a file:
# Keys
openssl genpkey -algorithm ED25519 -out ed25519.key
openssl pkey -in ed25519.key -pubout -out ed25519.pub
# Sign & verify
openssl dgst -sha256 -sign ed25519.key -out msg.sig message.txt
openssl dgst -sha256 -verify ed25519.pub -signature msg.sig message.txtCreate an X25519 key pair for key exchange:
openssl genpkey -algorithm X25519 -out x25519.key
openssl pkey -in x25519.key -pubout -out x25519.pub(Commands are for demo; in production, use well-maintained libraries and protocols like TLS, libsodium, age, Tink.)
Common Mistakes & Safe Defaults
- Do not roll your own crypto. Use vetted libraries.
- Avoid obsolete: DES/3DES, RC4, MD5, SHA-1, bare CBC without MAC.
- Never reuse nonces with GCM/CTR; ensure randomness/uniqueness.
- Use AEAD (AES-GCM or ChaCha20-Poly1305) for confidentiality and integrity.
- Prefer X25519 (key exchange) and Ed25519 (signatures) or RSA-3072+ if compliance requires RSA.
- Plan for post-quantum migration later (hybrid PQC/TLS when your stack supports it).
The approach followed at E Lectures reflects both academic depth and easy-to-understand explanations.
People also ask:
They solve different problems. Symmetric is faster and ideal for data; asymmetric enables key exchange and signatures. Use both via hybrid encryption.
AES-256 (or AES-128 if performance-critical), X25519/Ed25519, or RSA-3072+ for long-term certificates.
On devices without AES hardware acceleration (many mobiles/IoT) or where constant-time software performance matters.
No. ECC is faster/smaller; RSA remains widely supported and compliant. Many orgs use both depending on ecosystem constraints.
With GCM/CTR it lets attackers derive keystream relationships and recover plaintext or forge tags.
Don’t. RSA is for small secrets (session keys). Encrypt the file with AES, then encrypt the AES key with RSA (hybrid).